In a recent turn of events, Ledger, the prominent provider of hardware wallets, finds itself embroiled in a controversy surrounding its newly launched Ledger Recover feature. The optional service, aimed at aiding users in recovering their seed phrases, which grant access to their crypto wallets, has raised serious security concerns among the crypto community.
What is Ledger Recover?
The Ledger Recover service aimed to provide an additional layer of convenience by allowing users to recover their seed phrases in case of emergencies. To utilize this service, users are required to undergo identity verification by submitting their passport or national identity card for authentication. The process involves encrypting the seed phrase into three fragments, which are then distributed among Coincover, Ledger, and an independent backup service provider.
To regain access to their wallets, users must pass ID verification, after which two out of the three companies will send the encrypted fragments back to the user’s Ledger device. By combining and decrypting these fragments, the original seed phrase is revealed.
Implications and Security Concerns
The introduction of this feature has raised significant concerns among users, primarily due to two key implications regarding security.
Firstly, the involvement of three companies in storing encrypted private keys increases the risk of exposure to potential security breaches, social engineering, and identity theft.
However, the most concerning aspect is the potential exposure or extraction of the seed phrase from the device itself. The fact that the Ledger devices could have the private key extracted out of their secure element chip by a firmware update is highly alarming. The design of a hardware wallet is intended to ensure that the seed phrase never leaves the device, even in the event of a malicious firmware attack, thereby maintaining an “air gap” to prevent any unauthorized access. In fact, Ledger themselves tweeted this claim in Nov 2022:
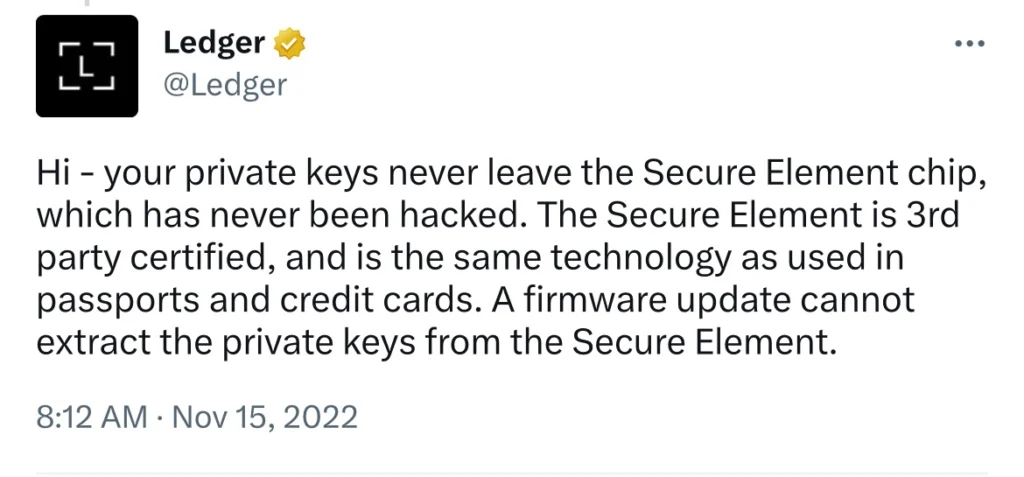
Further investigations have confirmed that the Secure Element chip can be programmed to send back any requested information. This programming requirement, essential for supporting new chains through new device applications, unfortunately leaves Ledger devices vulnerable to potential exploitation of a backdoor, emphasizing the significant security risks involved.
Closed-Source vs. Open-Source Code
One of the primary reasons behind the backlash faced by Ledger is the closed-source nature of its code, which prevented users and developers from scrutinizing the code repository.
Unsurprisingly many users and developers have since called out to ledger to open-source their code. In response to the outcry, Ledger has announced plans to open-source their code, except for the secure element code, which has to be kept secret.
How about Trezor?
In contrast, Trezor, another popular hardware wallet, has always operated with an open-source code. However, it’s important to note that open-source code doesn’t guarantee absolute security. Users must trust that white-hat hackers examining the code are more competent at auditing and identifying vulnerabilities than potential black-hat hackers.
Does this mean everyone should all use Trezors instead? Well, some Trezor devices are vulnerable to a high voltage glitching attack brought to light by Kraken security labs. This glitch only works if the attacker has physical access to the device itself.
Diversification and Mitigating Risks
Different hardware wallets have their own pros and cons, the fact that you are using a device created by another company already demands a minimal level of trust, and paper wallets are far from convenient and ideal. Considering the vulnerabilities highlighted in the Ledger controversy, it becomes evident that diversification is crucial not only for digital asset holdings but also for storage methods.
The key takeaway here is to diversify not just your digital assets holdings but also how and where you store them. By diversifying where your assets are stored, you can mitigate damage done when vulnerabilities are exploited.
This article provides information on the recent controversy surrounding Ledger’s new Ledger Recover feature and its implications for crypto storage. The views expressed in this article are based on the available information up to Jun 23, 2023 and may not reflect the current state of Ledger’s products or services. Therefore, readers are strongly advised to conduct further research and stay updated on the latest developments before finalizing their crypto storage strategies.
FEB recommends individuals to explore multiple storage methods and devices that align with their specific risk profiles. By staying informed, conducting thorough research, and adapting storage strategies accordingly, individuals can mitigate potential risks and enhance the security of their digital assets.






